iCompliant – IBM i Configuration Assessment Tool
-
 Assess all aspects of IBM i security from system configuration to object authorization
Assess all aspects of IBM i security from system configuration to object authorization -
 Execute compliance assessments as frequently as needed
Execute compliance assessments as frequently as needed -
 Implement defense-in-depth strategy that reduces the risk of exploitation even if a vulnerability occurs
Implement defense-in-depth strategy that reduces the risk of exploitation even if a vulnerability occurs
IBM i (formerly AS/400) systems play critical role in the business processes of their owners. However, security testing and monitoring of these systems usually doesn’t achieve the level we expect in case of Windows, Linux or Unix hosts.
Silent Signal’s proprietary iCompliant tool helps the secure operation and hardening of IBM i systems to minimize the attack surface. To satisfy the need of in-depth IBM i security assessments, the knowledge integrated into iCompliant is based on multiple pillars:
-
Checks for industry recommendations ensure compliance with security best practices and standards (PCI-DSS, SOX, COBIT, ISO 27002).
-
Hands-on penetration testing experience enables targeted hardening against practical attacks relying on weaknesses outside the usual scope of security standards.
-
The latest results of IBM i security research at Silent Signal are integrated to deliver exclusive defensive solutions.
iCompliant applies this knowledge to examine the overall security posture of its target systems, and deliver comprehensive results about weaknesses to remediate and settings to improve.
-
Modular Architecture
Audit checks can be enabled one-by-one for each individual target. Users can develop custom, system-specific checks either themselves, or with the assistance of Silent Signal experts.
-
Zero Dependencies
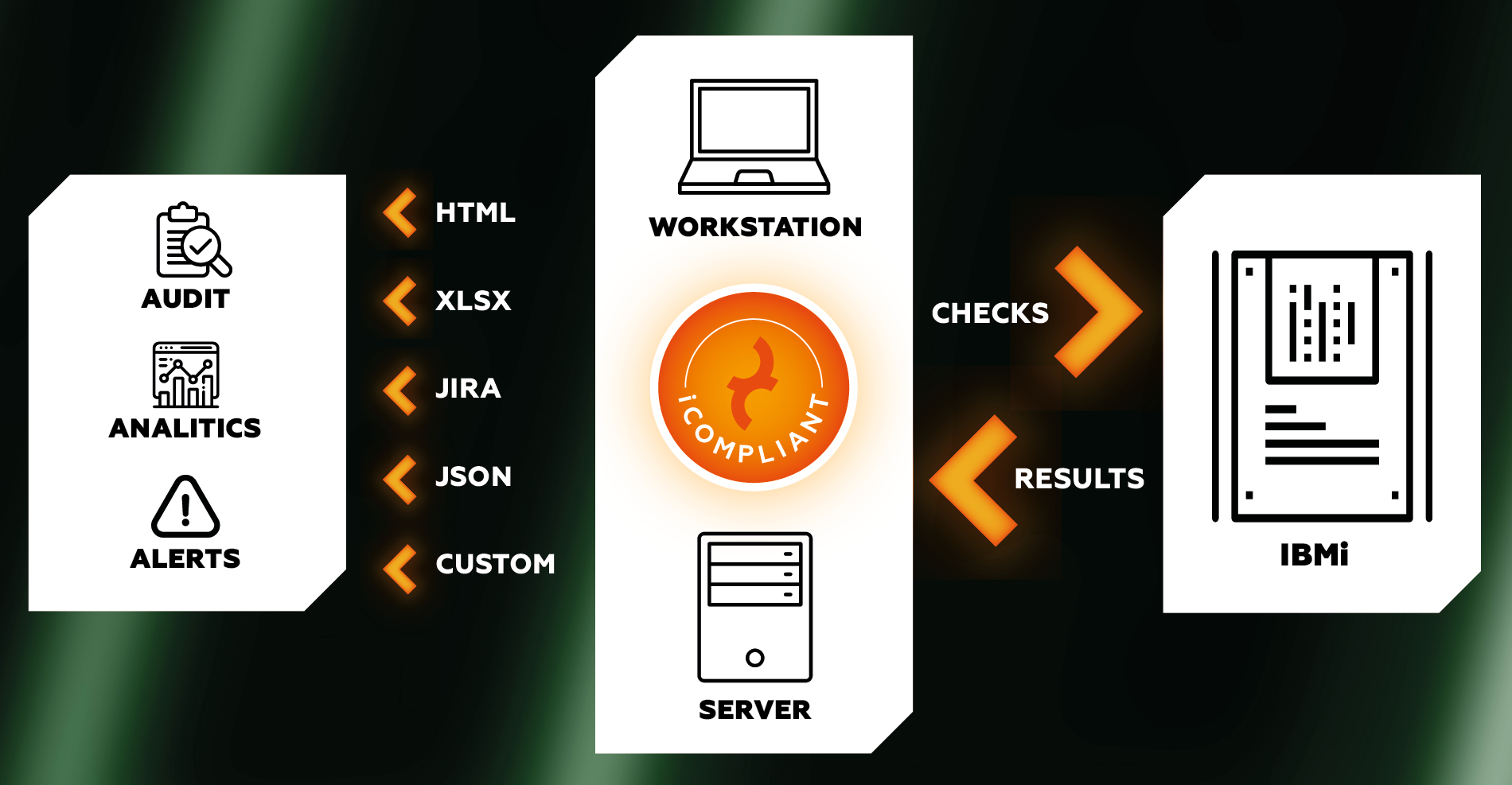
Security checks can be launched from workstations or servers, from Linux or Windows. No additional software is required on the target systems.
-
Time Well Spent
Clear issue descriptions and prioritization of findings based on hands-on offensive experience ensure that defenders will work on solving the right problems.
-
Supporting the Security Process
Flexible export formats allow easy delivery of findings to existing risk management systems. Guided questionnaires help the security team to obtain accurate information from system operators.
Executive summary
Table of contents
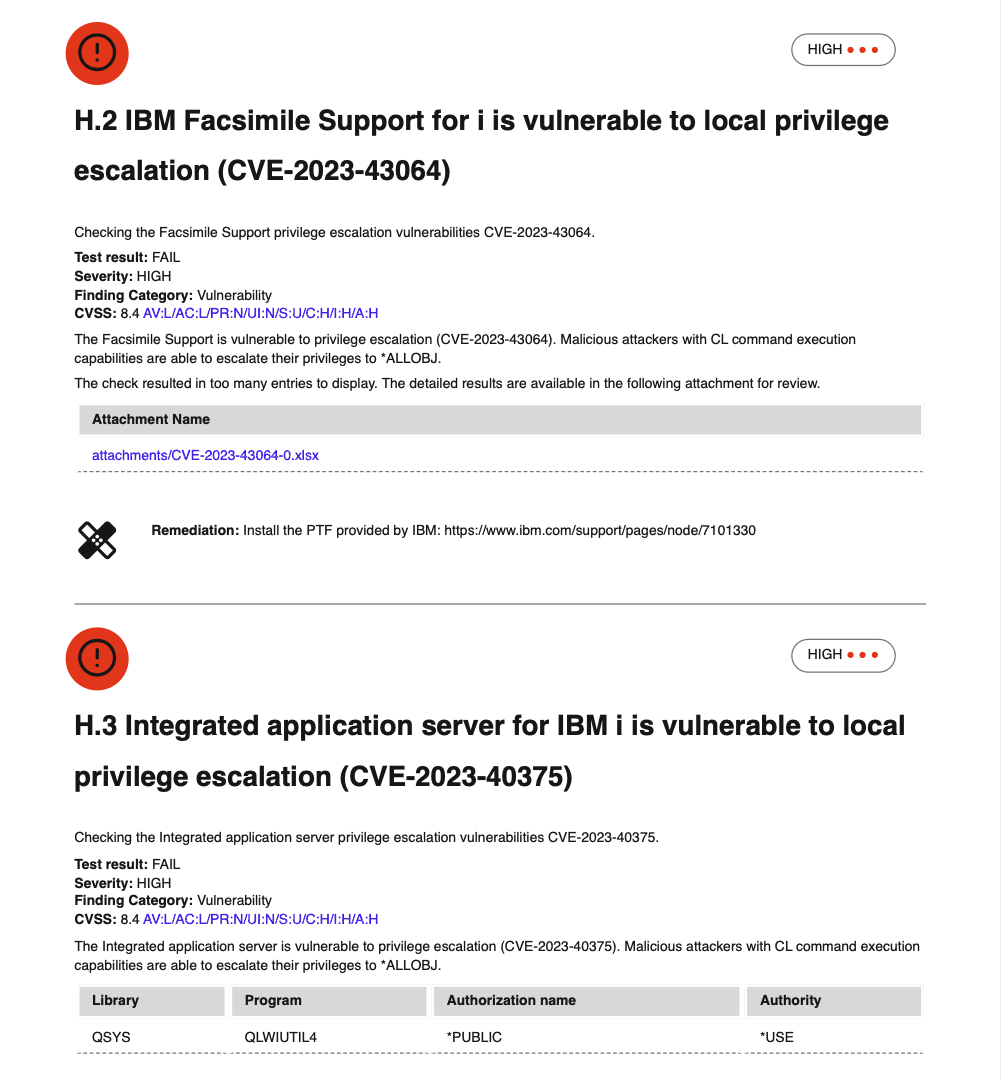
Example of failed audit items
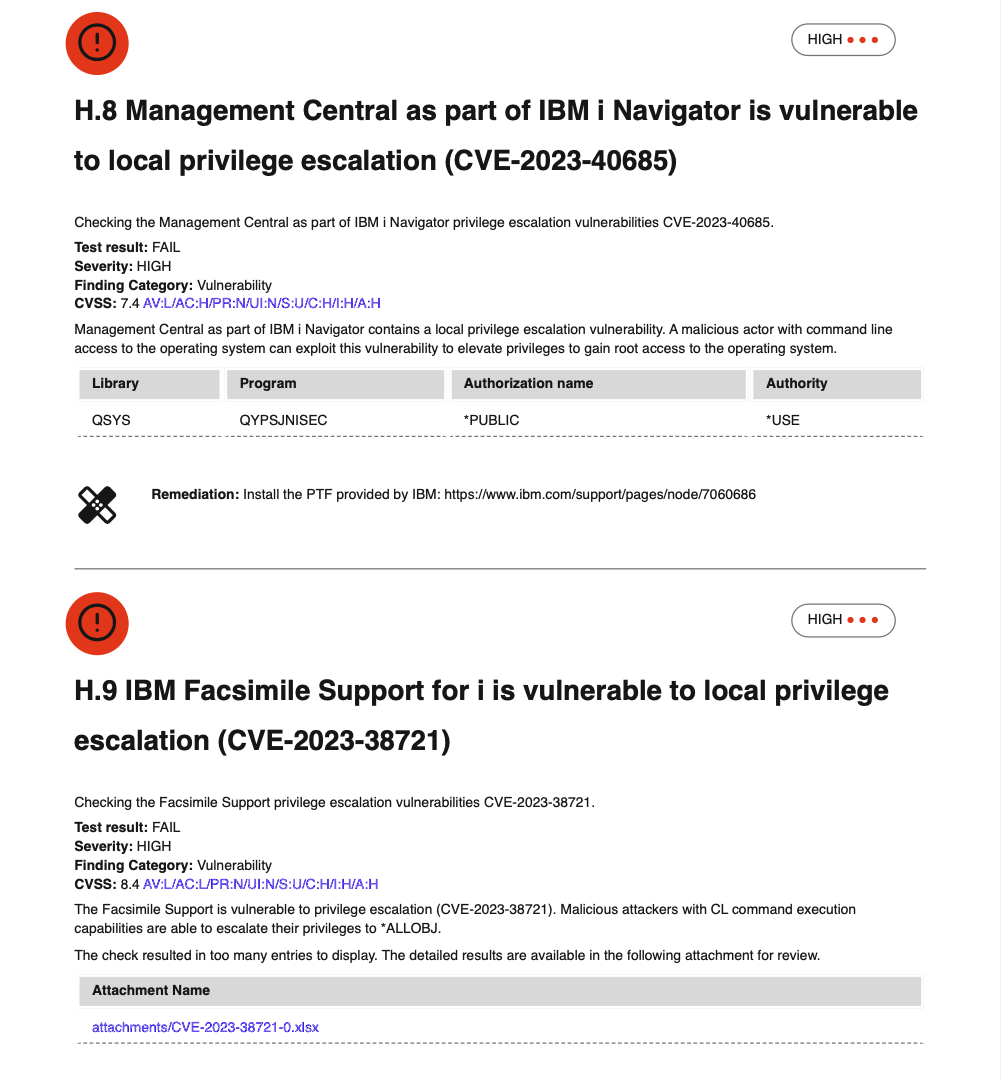
Another example of failed audit items
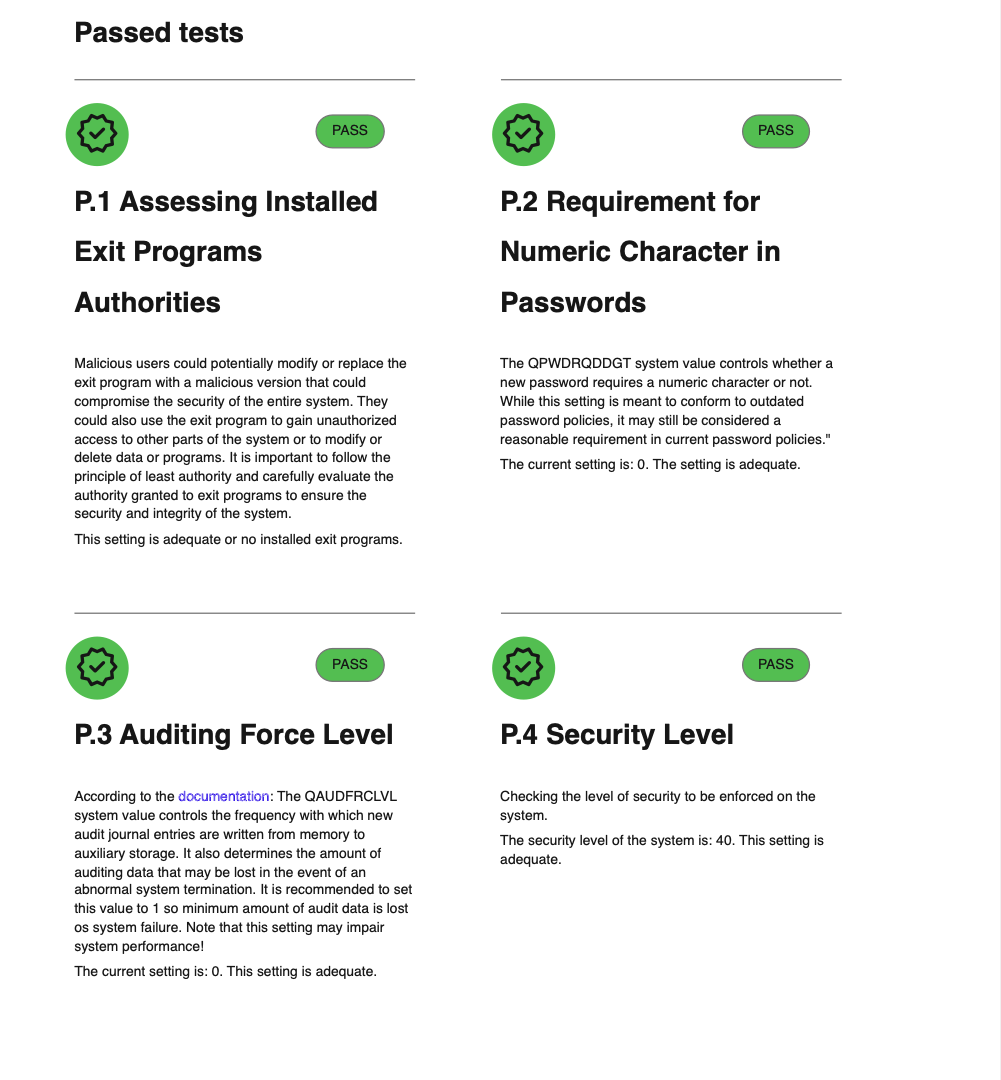
Example of passed audit items
Click on the images below to view screenshots from the report.
-
zoom_in
Click to view
FAQs
While iCompliant can be used to ensure compliance to best practices defined by organizations like CIS or IBM, the primary goal of the software is to provide practical guidance to implement defensive practices against all phases of the intrusion kill chain.
In its base configuration, iCompliant's knowledge-base incorporate hands-on experience from pentest projects and research to refine recommendations and prioritization.
Examples:
-
While some API's are accessible for all users by design, iCompliant checks hardened access controls since these API's are commonly used in privilege escalation exploits.
-
iCompliant provides information for local and remote attack surface reduction.
iCompliant is not a monitoring tool and it's not meant to provide real-time data. Some audit items check the state of large numbers of objects, that can take some time. For this reason, audit items are usually grouped so quick checks are executed more frequently, while heavier audits only run when load is low.
Examples:
-
A scheduled task can check system values every hour, while authorities on file objects are only checked once a month.
-
Select audit items can be executed on demand, e.g. after significant configuration updates.
Exit programs are important components of defense, but they are not silver bullets: not every interface can be protected by Exit Programs, and some vulnerabilities may be reached through allowed transactions. The principle of defense-in-depth dictates that we should anticipate that some of our controls fails, so we need to harden our systems in multiple layers.
Example:
-
Vulnerabilities of third-party applications generally can't be mitigated with Exit Programs.
Modern attacks commonly start from inside the corporate perimeter, exploiting client-side vulnerabilities or abusing human trust. Considering the frequency of incidents involving internal systems in general, the lack of data about IBM i systems only suggests that the industry simply doesn't have the means to detect such incidents.
Example:
-
The so-called 'Kemuri Water Company' incident proved that even usually low-skilled hacktivitst groups can and do target IBM i systems.
iCompliant is meant to be executed on external workstations or servers, and doesn't require extra software to be installed on the target IBM i systems.
Examples:
-
A scheduled task on a Linux server can periodically generate reports about IBM i systems.
-
SOC analysts can execute inidividual checks for human review from their Windows workstations.
Aside of standard integrations (Excel and JSON export; Jira integration) iCompliant can be extended so that it can support arbitrary export formats and API's. Contact us for a custom extension quote!
Examples:
-
Custom exporters can be created that can push results via a REST API.
-
Default JSON output can be transformed with standard tools to be loaded to any JSON-compatible ingestor.
iCompliant, as a framework allows creating custom audit items and fine-tuning results so they match the unique expectations and requirements of the target systems. Relevant audit items can be selected according to security requirements.
Examples:
-
Custom audit items can be created that check if critical business objects (files, data tables, source physical files, etc.) are only accessible by specific users of the company.
-
Verification of custom corporate password policy enforcement can be integrated to regular compliance checks.
Our customers can extend iCompliant with new audit items without limitation or additional cost. New audit items can be added by creating configuration files in an easy to understand, and fully documented format.
If creating audit items in-house is not an option for you, custom audit item development services are available - please contact us for more information about custom development services!
Subscriptions cover year-long periods, during which relevant updates and releases are delivered to customers. Subscription licenses are limited by the number of target IBM i systems iCompliant would work on.
Updates include:
- Feature updates of the iCompliant framework
- Bug fixes of the iCompliant framework (including potential security fixes)
- Updates to the already released Audit Items
- New Audit Items
Our standard license plans:
| Plan | Number of target LPAR’s | Subscription base period | Number of executions | Price |
|---|---|---|---|---|
| Enterprise Plan | Unlimited | 1 year | Unlimited | 30.000 EUR |
If you have unique needs, we can tailor custom license packs. Please contact us for custom licensing options!
Silent Signal performs unique security research focused on IBM i to uncover previously unknown vulnerabilities of the platform and Independent Software Vendors of the IBM i platform.
iCompliant Exclusive Vulnerability Feed provides access to the information uncovered by this research activity, so customers can mitigate vulnerabilities even before vendor fixes become available. The vulnerability feed subscription is available for select iCompliant Base Subscription customers at different levels:
Level 40 – 0-day Vulnerability Detection
In addition to the information provided in Level 0, customers receive Audit Items, so information about affected software can be collected automatically using the iCompliant framework.
Just like in case of any other Audit Item provided by Silent Signal, 0-day detection items will produce mitigation guidance as part of the final report if a vulnerability with no official patch is detected.
Level 50 – 0-day Vulnerability Demonstration
In addition to the items covered in Level 30 and Level 40, Level 50 subscription includes a demonstration attempt for any vulnerability included in the feed, on systems covered by the Base Subscription.
Demonstrations are performed by Silent Signal senior experts over remote network connections provided by the customer during agreed upon time frames.
The core IBM i and popular applications of Independent Software Vendors are included in the Exclusive Vulnerability Feed.
Example:
-
Your company uses a popular Exit Point Manager. With EVF Level 40 you get information about vulnerabilities that may affect this software and mitigation guidance before vendor patches are available.
Our basic support for iCompliant includes:
- Communication via e-mail
- 8x5 support hours (CET/CEST timezone)
- Next business day response to initial report
The problem of ransomware is not an IBM i specific problem that primarly affects IBM i systems at the integration points with the wider corporate infrastructure. For this reason, defending against ransomware requires strategies reaching over all platforms present in an organization. iCompliant contributes to the solution on the IBM i platform by attack surface reduction and verification of access controls.