IBM i Security Services
-

Myths
-

Facts
-
Our IBM i security publications
2025.10.22 IBM i LIBL Autopwn: Kill the Vulnerability Class 2025.09.04 Exploit development for IBM i 2025.01.21 Vulnerability Archeology: Stealing Passwords with IBM i Access Client Solutions 2024.06.29 Control Flow Integrity on IBM i (presentation, video) 2024.06.26 IBM i for Wintel Hackers (presentation, video) 2023.08.22 Technical Details of CVE-2023-30988 - IBM Facsimile Support Privilege Escalation 2023.07.03 Technical Details of CVE-2023-30990 - Unauthenticated RCE in IBM i DDM Service 2023.03.30 Booby Trapping IBM i 2023.01.20 Abusing Adopted Authority on IBM i 2022.09.28 Another Tale of IBM i (AS/400) Hacking 2022.09.05 Simple IBM i (AS/400) hacking -

Publicly available IBM i vulnerabilities reported by us
-

News articles and videos regarding our IBM i security research
- news ACS Password Leaks Are A Security Issue On IBM i
- news Attackers Exploit IBM i Access Client Solutions on Windows 11 To Steal Passwords
- news Ethical hackers uncover misconfiguration vulnerabilities in the IBM i platform
- news Ethical Hackers Discuss Penetration Work On IBM i
- news 2023: An IBM i Year in Review
- news Spooky New Security Vulns Lurking on IBM i
- news Silent Signal Launches iCompliant to Provide Elevated Security for IBM i System Users
- news Midsummer Security Indicators: Hot and Gloomy
- news Serious New IBM i Vulns Exposed by Silent Signal – More On the Way
- news New “High Priority” DDM Vulnerability Affects IBM i
- news Silent Signal Discovered a Critical Vulnerability in IBM i System – CVE-2023-30990
- smart_display IBM Technology UKI Brunch and Learn – What You Can Do With An IP Address
- news White Hats Completely Dismantle Menu-Based Security
- news Pen Tester Silent Signal Targets IBM i
Assessment and Remediation
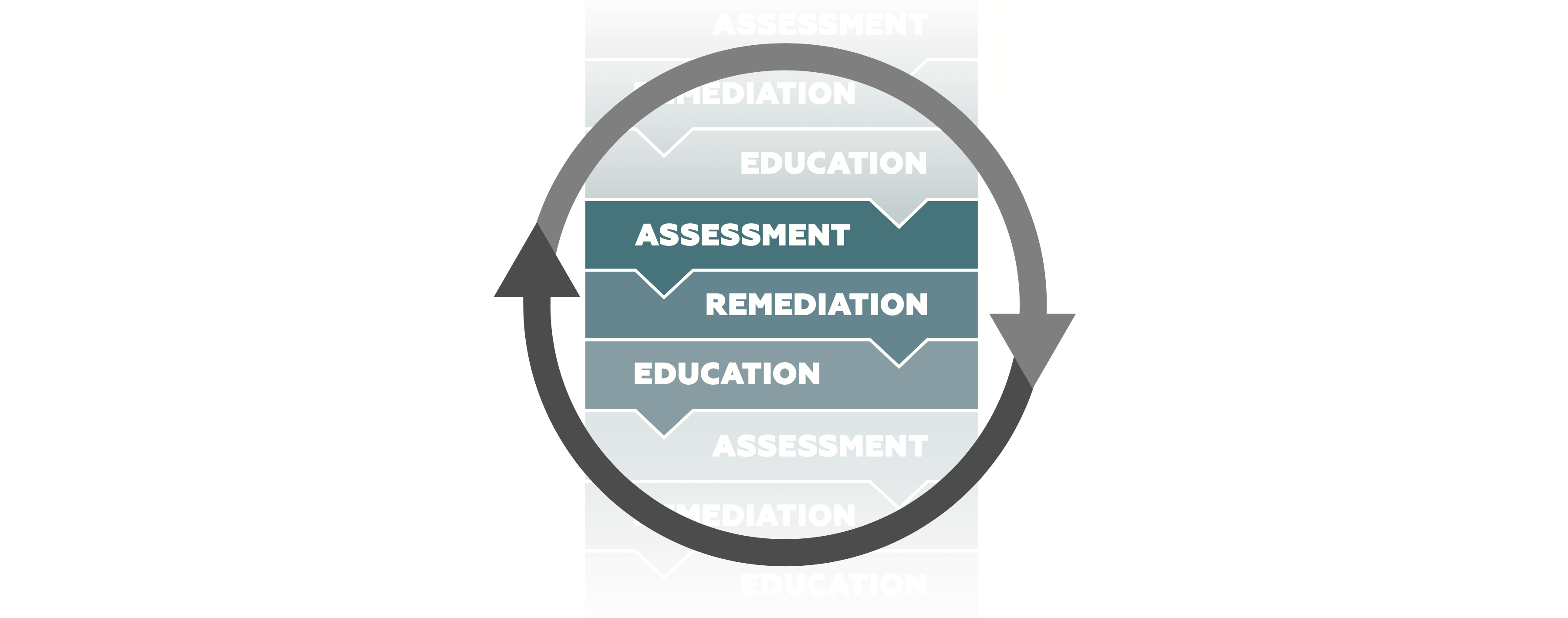
| Penetration testing | iCompliant | ||
|---|---|---|---|
| star | Objective | identify and exploit vulnerabilities | assess and review the security configurations |
| bolt | Automation | manual testing and human-driven analysis | automated process using specialized tools |
| assistant_direction | Approach | simulate real-world attacks | comprehensive examination of the system |
| monitor_heart | Level of Intrusiveness | intrusive and aggressive testing | non-intrusive |
| manage_history | Frequency | periodically or before major system updates | regularly to maintain the security of systems |
| frame_inspect | Scope | focuses on specific targets or applications | covers the whole system |
| hourglass_bottom | Time and Resources | time-consuming and resource-intensive | quicker and requires fewer resources |
| contrast | Testing Methodology | mix of black-box, grey-box testing | white-box audit |
| summarize | Report | vulnerabilities, impact, remediation | vulnerabilities, impact, remediation |
| payments | Cost | more expensive due to the manual efforts and expertise | often more cost-effective |
Education
-

IBM i training
Our IBM i security trainings are the ultimate resource for proactively securing IBM i systems. Led by experienced instructors with extensive knowledge of IBM i penetration testing, security research, and industry best practices, our trainings are designed to help IT professionals of all levels stay ahead of the curve when it comes to securing critical systems and data.
Our trainings enable security professionals to get up to speed with IBM i and its security features. We introduce the platform through hands-on exercises, and show how exploits are connected to well-known attacker techniques, allowing quick adoption of defensive concepts.
Learn more about our IBM i security training...
Request a demo, pentest or webinar
-

LIVE IBM i HACKING – ON-DEMAND WEBINAR
Demystifying IBM i System SecurityWhy IBM i System needs to be secured, and why wasn’t it an issue in the past 35 years?
We have proven that breaking into IBM i Systems from a remote location and escalating access rights to a privileged user is possible and can take less than a minute for a malicious actor. We did it. However, we are white hackers and reported more than 11 critical vulnerabilities so far, all vendor-patched with CVEs.
It’s time to shift your paradigm: enlighten the black hole in your IBM i System – we show you why and how.
CIOs and CISOs have been challenged by securing their mission-critical data kept in their old-time proven solutions, operating in the heart of their infrastructure, such as the IBM i System. Without the necessary tools, it’s impossible to have visibility in their traditional systems.
Key takeaways – what you will learn:
Speakers:
